North Korean users cannot access the world-wide-web, not even the global internet, but rather, they can only enter into the intranet (Kwangmyong) which is a private network. The intranet they use was established in the early 2000s. To add, NK’s domain country code is .kp, and was claimed in September 2007. Currently, it is active, and its intended use is with North Korean officials and businesses. Additionally, nearly all of North Korea’s assisted internet traffic is routed by China. As of now, only 30 addresses are available and some contain specialized abbreviations, or are blocked off entirely.
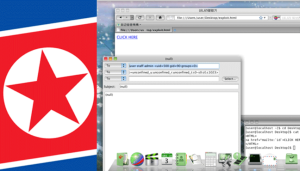
Red Star OS is a government controlled operating system designed to surveil users and monitor web activity. Given NK’s retroactive network, it may be prone to vulnerabilities because of its utilized four ipv4 subnets.

Very few citizens are authorized to use the internet, and it can be inferred many citizens are not aware that it exists. Or have not even experienced the operating system itself at all, but it can be injected via a disc. Citizens are believed to only use the web for government and research purposes. Only a select few are permitted to use the intranet, and must be regularly checked by the authorities.
The browser they use is a heavily modified version of Mozilla Firefox, an open-source project, and it is called Naenara; certain HTML and JavaScript elements may not load properly due to its retroactive configuration. Since the browser is heavily modified, some researchers have suggested that browser-related exploits, like cross-site scripting (XSS) or other web-based vulnerabilities, could be possible within the local intranet environment.
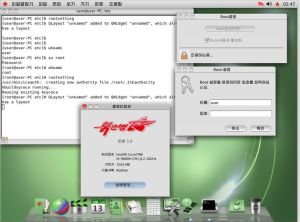
Overall, the software’s user interface (UI) is inspired by Apple’s OS X, and widget icons are green. Which perhaps, pays homage to Kim Jong Un’s fondness for Apple products. Each time a user imports/exports a file, a tracked identifier is set automatically. This is done to track distribution of foreign media, which the regime deems “illegal.” That means that, even if a file is shared or copied, it can be traced back to the original creator.
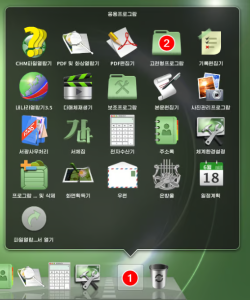
While there is no known widespread method to completely bypass this system, researchers have noted that certain file operations (such as using non-native file systems or advanced file management techniques) might make the watermark harder to track or less reliable. And there are other applications that users can open up too on Red Star OS.
This software is generally not safe for user consumption, and precautionary measures should be taken. It is presumed to be risky, and Red Star OS has been speculated to have spyware-like features from its programmed infrastructure. Although for those who’ve downloaded Red Star OS, it is recommended to do it with a Virtual Machine (VM) instead for security reasons.

Like most Linux-based systems, Red Star OS has its own modified Linux kernel. This kernel controls the system’s resources and ensures that only certain programs can be run. Since Red Star OS is still built on Linux, it shares many vulnerabilities inherent to Linux systems. Exploits that work on Linux systems could potentially be adapted to Red Star OS.
Ethical hackers have found that the encryption systems used in Red Star OS are custom-built and may not follow conventional encryption standards. If researchers could discover flaws in the encryption implementation, it might be possible to decrypt files or intercept communications. However, there have been no major reports of successful encryption-breaking exploits, and any such activity would be highly technical and risky.
Behind the scenes, though, the regime has invested heavily in cybersecurity and cyber warfare capabilities, leveraging a hidden tech base to develop sophisticated hacking tools. The country also focuses on cyber espionage, infiltrating foreign governments and companies to extract information related to military, economic, and political strategy.
North Korea has training programs where young people are selected and sent to specialized institutions like the Pyongyang University of Science and Technology (PUST) and other state-run programs. These institutions are designed to teach students advanced tech skills, including programming, cryptography, and network security.
Despite the country’s isolation, many hackers have access to global tech trends and cyber tools. North Korean hackers are proficient in using open-source tools and modifying them for their purposes. For example, malware frameworks like Meterpreter or Cobalt Strike can be customized to bypass security systems and infiltrate networks.
There are reports that some hackers have been trained in foreign countries (like China, Russia, or even through self-study). As of late 2023, North Korea has upgraded from 3G to 4G internet, although this is limited to major cities and their capital, Pyongyang.
North Korea’s approach to technology, including its cyber operations and the hiring of skilled hackers, is indeed fascinating—especially given that the country’s public-facing technology is often outdated and heavily controlled.
This juxtaposition highlights the paradox of North Korea’s technological landscape, where state-of-the-art cyber capabilities coexist with a tightly controlled and outdated public tech infrastructure.



















![JPEGMAFIA & Danny Brown — Scaring The H*es (Video-Game/Album Cover) [CENSORED]](https://www.southlakessentinel.com/wp-content/uploads/2023/12/SCARING-THE-H0ES-VIDEO-GAME-COVER-1200x802.jpg)





